Cmmi continuous Cmmi common process models areas specific different core representation schematic elements consultant Cmmi model: graphical representation
(PDF) CMMI V2.0 and the CyberSecurity Maturity Model
Cmmi template — magical presentations. fast. easy. beautiful
What are the different cmmi models that are available at this time
[diagram] basic network diagram schematicsUnderstanding the core concepts of capability maturity model Cmmi model components in the continuous representation [1]Cmmi pyramid staged.
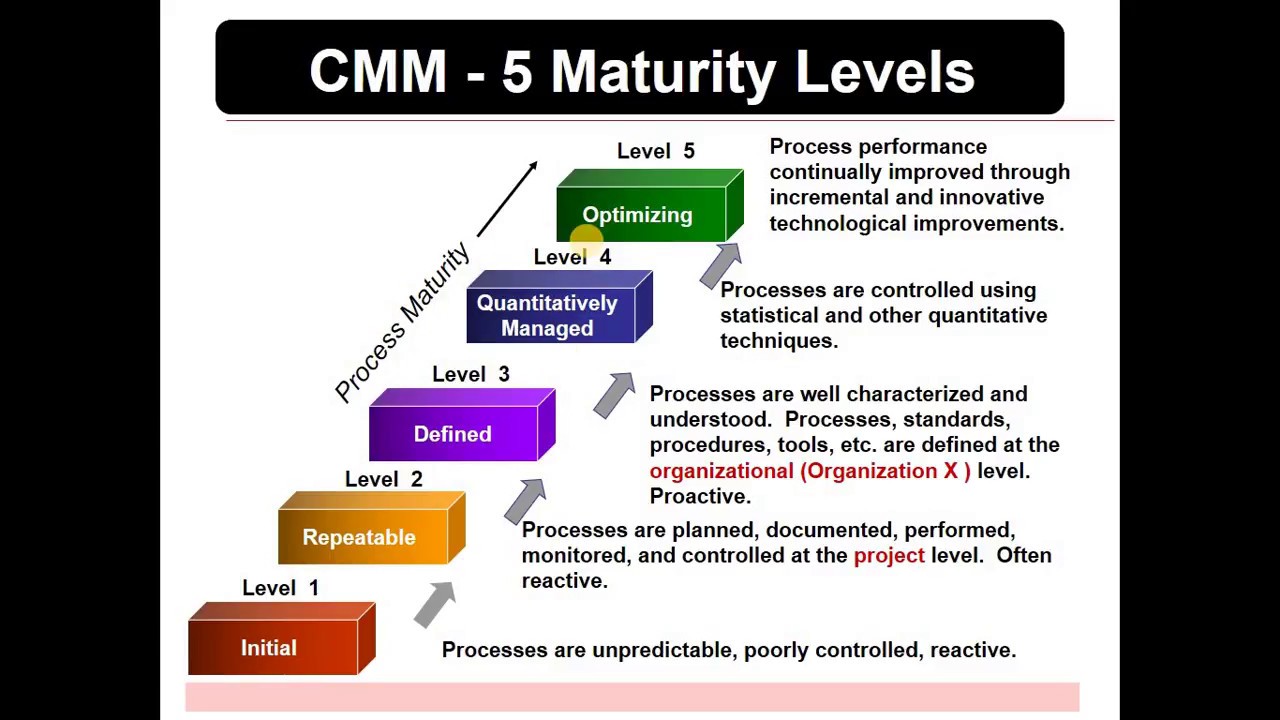
What is cmm in software project management2. the design of cmmi model Mapping cmmi maturity capability levels • plays-in-businessConceptual diagram of cmmi project planning pa..

Cmmi components interactions numbered
Part of the sample model with security components.Security network diagram control computer diagrams devices networks access model solution encryption secure examples cloud example architecture conceptdraw system software Cmmi model with a continuous representation.Capability maturity model integration (cmmi) [16].
Review chapter 14. explain the cmmi model with an example.reference .docxجزوه cmmi introduction امیرهوشنگ تاجفر The structure of cmmi v1.3Improve your capability at delivering software and systems – cmmi quick.
Important projects
Simplified security model.How to use cmmi to improve your information security controls Organization development maturity modelsCapability maturity model integration (cmmi).
Cmmi levels maturity process five assessment level improvement model management models corrective using analysis benefits business representation projects important herdingCmmi model (see online version for colours) Cmmi (capability maturity model integration) checklistThe cmmi model was developed by.
Network security model
Cmmi +safe1 below shows the continuous view of the cmmi: Improvement cmmiHistory of cmmi models.
The cmmi model components(pdf) cmmi v2.0 and the cybersecurity maturity model Cmmi model components and their interactions (numbered 1, 2, 3, and 4.





![CMMI model components in the continuous representation [1] | Download](https://i2.wp.com/www.researchgate.net/profile/Zahoor_Ul_Islam2/publication/277121709/figure/download/fig7/AS:294465106399241@1447217360760/CMMI-model-components-in-the-continuous-representation-1.png)